
Cyber Security
DON'T WAIT UNTIL IT'S TOO LATE
Don't Wait Until It's Too Late

Cyber Security Protection & Backup in Cheshire for SMEs
Have you considered the impact of a ransomware attack, virus infection, or catastrophic hardware failure on your business? No organisation is immune, and smaller businesses are often seen by cybercriminals as easy targets due to limited investment in cyber security.
That’s why robust cyber security for your computers and servers, along with dependable backup systems, is crucial. With CED Technology, you receive not just protection, but also peace of mind. Our 24/7 monitoring, threat detection and response, and system backups safeguard your data, while consistent software updates and patching guarantee seamless, reliable operations. With the assurance that your business is secure, you can concentrate on growth with confidence, rather than worry.
Explore our
blog post
for an in-depth look at why robust cyber security matters.
Cyber Security Features
Our cyber security plans provide comprehensive protection for your business, covering all the essential features needed to safeguard your digital assets and operations.
We ensure that your business remains resilient against cyber risks, giving you peace of mind and allowing you to focus on growth without worrying about vulnerabilities.
Remote Monitoring and Management (RMM)
What is RMM?24/7 oversight of your IT infrastructure to detect and resolve issues proactively. Automated updates are deployed seamlessly to endpoints, with minimal user interaction—only requiring approval for a reboot if necessary.
If you would like a further explanation of what RMM is and why it is so important, please click on the link.
Software Updates & Patching
Ensures your computer is always up to date by regularly applying essential updates and patches for your operating system, applications, and hardware.
This process is crucial for maintaining security, compliance, and optimal performance, protecting your business from cyberattacks and potential data loss.
Antivirus & Malware Protection
A powerful yet lightweight solution offering reliable protection against viruses and malware for all your endpoints.
This advanced tool is designed to efficiently scan, detect, and eliminate harmful software, ensuring your systems remain secure without compromising performance.
Whether it's protecting individual PCs or critical servers, it provides comprehensive defence across your entire network. With real-time monitoring, automatic updates, and a minimal impact on system resources, this solution delivers continuous protection against emerging threats.
Ransomware Detection
Uses behavioural analysis to monitor for the presence of crypto-ransomware on endpoints, alerting you immediately if a device is infected. The infected device can then be isolated if necessary to prevent the ransomware from spreading further.
Endpoint Detection and Response (EDR)
What is EDR?EDR continuously monitors end-user devices, automatically detecting and responding to cyber threats such as ransomware and malware.
Read our blog post for an in-depth look at what EDR is and why it is essential for every business.
Endpoint Backup
A cloud-based backup and recovery solution tailored for Windows PCs or laptops. It allows for the restoration of individual files or the entire backup image to a new device of the same spec without the need for additional equipment. Backups are taken incrementally each day.
Backups of folders managed by cloud services such as OneDrive, Google Drive, or Dropbox are not included, as these are already backed up by the respective providers.
Plans start from 150GB core system storage capacity per device with custom sizes and server backup options available on request.
Remote Support Assistance
See IT Support ServicesOur technicians can provide remote access support as part of the package, ensuring a swift resolution to your computer issues. Whenever you encounter any problems with your computer, we’ll be ready to log in remotely and resolve them for you.
Remote computer support is also available as part of the IT Support Services we offer.
The Benefits of Cyber Security
A robust cyber security plan provides your business with far more than just protection—it delivers a range of benefits that enhance operational resilience, safeguard your reputation, and ensure long-term success.

Automated Updates
System and software updates are automatically managed, reducing the need for manual intervention and ensuring your devices remain secure and up to date.
Security Policy Enforcement
Ensures consistent enforcement of company-wide security policies, enhancing overall compliance and reducing risks.
Proactive Maintenance
Regular monitoring and proactive maintenance help prevent issues before they impact operations, minimising downtime and improving productivity.
Ransomware Detection
Uses behavioural analysis to monitor for the presence of crypto-ransomware on endpoints, alerting you immediately if a device is infected. The infected device can then be isolated if necessary to prevent the ransomware from spreading further.*
Flexible Recovery Options
Enjoy peace of mind with options for partial or full system restoration in the event of data loss or catastrophic failure.
Cost Control
No surprise bills – just a predictable investment in your security.
With everything included, there’s no need to buy extra antivirus or malware tools, helping you keep IT costs under control.
Business Continuity
Unplanned downtime doesn’t just cost money – it can damage client relationships and your peace of mind.
With enhanced cyber security, that risk is greatly reduced. And if the worst should happen, reliable backups and rapid recovery mean your business is back up and running with minimal disruption.
Improved Compliance
Regular patching and updates help maintain compliance with industry standards and regulations, protecting your business from potential legal and financial repercussions.
Scalability
Easily scalable to meet the growing needs of your business, accommodating additional devices and servers without hassle.
Reduced IT Overhead
Streamlined management and support reduce the burden on your in-house IT team, allowing them to focus on strategic initiatives.
Why Choose CED Technology for Cyber Security?
With countless cyber security service providers available, it’s important to recognise that not all offer the same level of protection, expertise, and service quality. So, what makes CED Technology stand out from the competition?
It’s our commitment to providing tailored, business-focused security solutions, proactive threat detection, and expert support—ensuring that your IT systems remain secure, efficient, and resilient against ever-evolving cyber threats.
Why Choose CED Technology for Cyber Security?
With countless cyber security service providers available, it’s important to recognise that not all offer the same level of protection, expertise, and service quality. So, what makes CED Technology stand out from the competition?
It’s our commitment to providing tailored, business-focused security solutions, proactive threat detection, and expert support—ensuring that your IT systems remain secure, efficient, and resilient against ever-evolving cyber threats.

Experience
With more than 25 years in the IT industry, we truly understand our field! Partnering with CED Technology gives you the confidence of receiving assistance from a company that has a solid history of consistently delivering exceptional support.
Expert Guidance
Our team will assess your cyber security needs and recommend the best solutions for your business.
Customised Solutions
Tailored strategies to meet the unique requirements of your organisation.
Reliable Support
Count on us for ongoing support and monitoring to ensure the integrity and security of your data.
Peace of Mind
Rest easy knowing that your critical data is safely backed up and ready for recovery when needed.
Affordability
Our Cyber Security Protection and Backup services are budget-friendly, allowing for individual elements to be included or excluded as needed.
Affordable Cyber Security Plans
We provide a variety of standard plans that encompass a range of features from our Cyber Security Protection and Backup services. Pricing is based on the number of users and devices protected.
Unlimited remote IT support can be added to any of the plans.
For specific server protection options, please reach out to us for a personalised quote.
CYBER BRONZE
✅ 24/7 Remote Monitoring & Management
✅ Software & Driver Patching
❌ Endpoint Detection & Response
❌ Antivirus Protection
❌ Malware Protection
❌ Ransomware Prevention
❌ Computer Backup (up to 150GB)
CYBER BRONZE+
🧑💻
Add Unlimited Remote IT Support
CYBER SILVER
✅ 24/7 Remote Monitoring & Management
✅ Software & Driver Patching
✅ Endpoint Detection & Response
✅ Antivirus Protection
✅ Malware Protection
✅ Ransomware Prevention
❌ Computer Backup (up to 150GB)
CYBER SILVER+
🧑💻
Add Unlimited Remote IT Support
CYBER GOLD
✅ 24/7 Remote Monitoring & Management
✅ Software & Driver Patching
✅ Endpoint Detection & Response
✅ Antivirus Protection
✅ Malware Protection
✅ Ransomware Prevention
✅ Computer Backup (up to 150GB)
CYBER GOLD+
🧑💻
Add Unlimited Remote IT Support
Order today from one of our standard plans, or complete the form to receive a customised quote tailored to your business and number of users.
Cyber Enquiry Form
Thank you for sending us your enquiry.
We will get back to you as soon as possible.
You can now leave this page.
CED Technology
Oops, there was an error sending your message.
Please try again later.
Miercom Independent Report
CED Technology employs the Datto suite of Endpoint Detection and Response (EDR) and Antivirus (AV) solutions.
Datto engaged Miercom, a leading third-party security testing and certification facility, to conduct a private evaluation to assess and benchmark the effectiveness of the products in protection and detecting actual threats with a focus on the latest malware strains and the most employed infection vectors.
Key Findings:
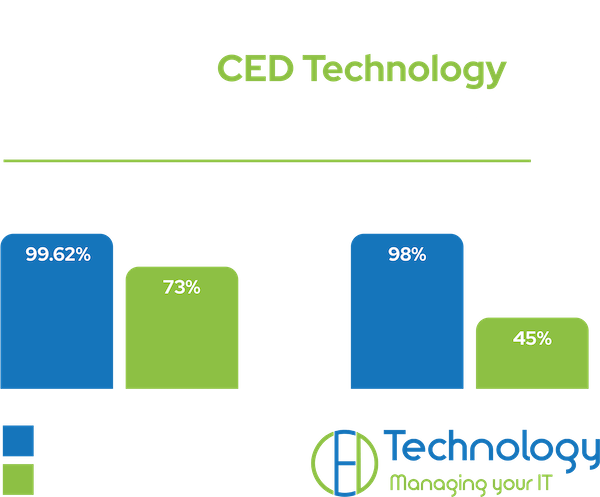
- Overall Malware Efficacy:
Datto EDR with Datto AV demonstrated an overall malware detection efficacy rate of 99.62% in detecting and neutralising malware threats, compared to the industry average of 73% of products in this class.
- Zero-Day Threat Detection:
The study revealed that both Datto EDR and Datto AV achieved a 98% detection rate for zero-day threats, which is more than double the industry average for products in this class of 45%.
- Proven Advanced Threat Detection: Datto exceeded expectations for detecting fileless threats and ransomware while effectively isolating infected endpoints. Their solutions have proven effective in mitigating advanced evasive, advanced persistent, and polymorphic threats.
As a result of this study, Datto EDR and AV received the 'Miercom Certified Secure' certification for demonstrating security excellence..

Cyber Essentials
Gaining Cyber Essentials certification requires demonstrating that your business has effective data controls and security measures in place – and strong cyber security defences make up a significant part of that.
From managing access to securing devices and preventing malware, the certification process focuses heavily on proving that your systems are protected against common cyber threats. By putting the right safeguards in place, you not only work towards certification but also strengthen your overall security posture.
Penetration Testing
In addition to our core cyber security solutions, we also offer penetration testing in association with our strategic partner, Mongoose Cyber Security.
This service helps identify and address potential vulnerabilities before they can be exploited, giving you a clearer understanding of your security posture.
Regular testing strengthens your defences, reduces security risks, and ensures your business stays protected against evolving cyber threats.
Free Cyber Security Newsletter

We offer weekly cyber security news updates, featuring the latest threats and essential security advice delivered straight to your inbox.
To subscribe to our FREE Cyber Security Newsletter, please complete the form with your contact details.
Contact Us
Thank you for providing your details.
You will begin to receive the weekly CED Technology cyber news bulletin from the next edition.
CED Technology
Oops, there was an error sending your message.
Please try again later.
Don't Delay
Don't leave your data and business at risk. Trust CED Technology for comprehensive cyber security, protection and backup solutions tailored to your business. Contact us today to schedule a consultation and safeguard your valuable information.

Cyber Security FAQs
What cyber security services do you provide?
We provide layered cyber security protection including antivirus, endpoint detection and response (EDR), ransomware protection, and monitored data backups. This reduces the risk of cyber attacks, data loss, and downtime.
Is cyber security necessary for small businesses?
Yes. Small businesses are frequently targeted by cyber criminals. Even a single incident can result in lost data, business disruption, and reputational damage.
Do you secure Microsoft 365 accounts?
Yes. We help secure Microsoft 365 by configuring user access, enforcing strong passwords, enabling multi-factor authentication, and applying security best practices.
What happens if we are affected by ransomware?
Our focus is prevention, but if an incident occurs we assist with containment, system recovery, and restoring data from secure backups to minimise downtime.
How often is our data backed up?
Backup schedules vary depending on your requirements, but most systems are backed up daily or more frequently. Backups are monitored to ensure they complete successfully.
Where is backed-up data stored?
Data is stored securely using encrypted storage, typically within UK or EU data centres depending on the service used and compliance needs.
Can you restore individual files or full systems?
Yes. We can restore individual files, folders, or entire systems depending on what is required and the system being restored to.
Protecting Businesses Across Cheshire
While we are proudly based in Winsford, CED Technology specialises in providing essential cyber security and data protection services tailored for small to medium-sized businesses throughout the entire county and beyond. Our expert team regularly assists organisations in major areas such as Chester, Warrington, and Macclesfield, as well as the bustling business communities of Crewe, Northwich, Runcorn, Widnes, and Ellesmere Port. We deliver comprehensive protection, from Ransomware Prevention, Antivirus, and EDR (Endpoint Detection and Response) to robust Data Backup and Recovery solutions. Our commitment extends to towns like Knutsford, Sandbach, Congleton, Middlewich, Nantwich, Holmes Chapel, and Tarporley, ensuring your digital assets are safe across all of Cheshire, including nearby areas like Stoke-on-Trent.
Explore our other services
Disclaimer and Limitation of Liability:
CED Technology offers Cyber Security Protection & Backup services to help strengthen the security and reliability of your IT infrastructure. While we utilise advanced technology and industry best practices to protect your systems and data, it is important to note that no cyber security or backup solution can provide complete protection against all threats or fully eliminate the risk of data loss or damage. As such, these services are provided subject to our standard terms and conditions, which can be found here:
Terms & Conditions

